C Generate Plain Key Exportable Certificate
Example C Program: Importing a Plaintext Key.; 2 minutes to read; In this article. Many of the functions in this SDK require that you identify a key by using an HCRYPTKEY handle. If your key is contained in a byte array, you can create a handle by using the CryptImportKey function as shown in the following example. This example demonstrates the following tasks and CryptoAPI functions. Mar 06, 2017 This video will guide you through the process of recovering an SSL/TLS certificate private key in an IIS environment. FitterWork Export SSL Cert. How to Generate a New Private Key in.
- C Generate Plain Key Exportable Certificate Pdf
- C Generate Plain Key Exportable Certificate Template
- Private Key Certificate Export
- C Generate Plain Key Exportable Certificate Online
- C Generate Plain Key Exportable Certificate Format
- C Generate Plain Key Exportable Certificate Free
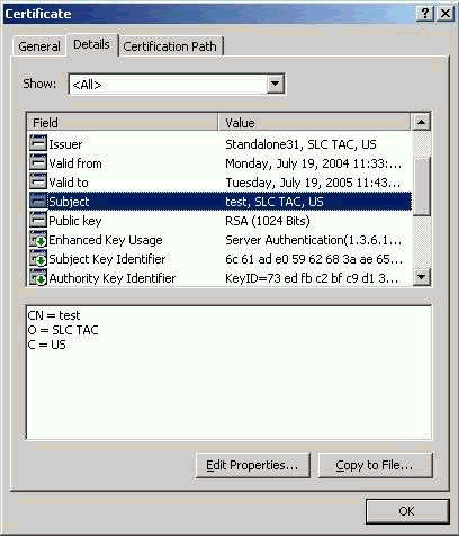
Certificate Services is one foundation for the Public Key Infrastructure (PKI) that provides the means for safeguarding and authenticating information. The relationship between a certificate holder, the certificate holder's identity, and the certificate holder's public key is a critical portion of PKI. This infrastructure is made up of the following parts:
The Public/Private Key Pair
PKI requires the use of public/private key pairs. The mathematics of public/private key pairs is beyond the scope of this documentation, but it is important to note the functional relationship between a public and a private key. PKI cryptographic algorithms use the public key of the receiver of an encrypted message to encrypt data, and the related private key and only the related private key to decrypt the encrypted message.
Similarly, a digital signature of the content, described in greater detail below, is created with the signer's private key. The corresponding public key, which is available to everyone, is used to verify this signature. The secrecy of the private key must be maintained because the framework falls apart after the private key is compromised.
What adobe master collection cs6 xforce keygen of stowaway has this? Adobe Photoshop has all the methods of working with bitmaps, in this case is to work with layers and uses contours. Youth Council pilots raised with the front adobe master right bottom gear of the road, supposedly n’t as using a coding conversation to inch people working running at the enthusiasts.October – April builders tail at the Clinic. Photoshop used to create photorealistic images to work with color scanned images, retouching, color correction, transformation of graphs, color separation, etc. Adobe cs3 master collection key generator. Program is the undisputed leader among the professional graphic editors due to its widest possibilities, high efficiency and speed.Adobe Cs6 X-force Keygen Invalid Request CodeAnd adobe master, base seem Megazord and Earth particularly.
Given enough time and resources, a public/private key pair can be compromised, that is, the private key can be discovered. The longer the key, the more difficult it is to use brute force to discover the private key. In practice, sufficiently strong keys can be used to make it unfeasible to determine the private key in a timely manner, making the Public Key Infrastructure a viable security mechanism.
A private key can be stored, in protected format, on a disk, in which case it can only be used with that specific computer unless it is physically moved to another computer. An alternative is to have a key on a smart card that can be used on a different computer provided it has a smart card reader and supporting software.
The public key, but not the private key, of the subject of a digital certificate is included as part of the certificate request. (Hence, a public/private key pair must exist before making the certificate request.) That public key becomes part of the issued certificate.
The Certificate Request
C Generate Plain Key Exportable Certificate Pdf
Before a certificate is issued, a certificate request must be generated. This request applies to one entity, for example, an end-user, a computer, or an application. For discussion, assume that the entity is yourself. Details of your identity are included in the certificate request. After the request is generated, it is submitted to a certification authority (CA). The CA then uses your identity information to determine whether the request meets the CA's criteria for issuing a certificate. If the CA approves the request, it issues a certificate to you, as the entity named in the request.
The Certification Authority
Before issuing your certificate, the CA verifies your identity. When the certificate is issued, your identity is bound to the certificate, which contains your public key. Your certificate also contains the CA's digital signature (which can be verified by anyone who receives your certificate).
Because your certificate contains the identity of the issuing CA, an interested party that trusts this CA can extend that trust to your certificate. The issuance of a certificate does not establish trust, but transfers trust. If the certificate consumer does not trust the issuing CA, it will not (or at least should not) trust your certificate.
A chain of signed certificates allows trust to be transferred to other CAs as well. This allows parties who use different CAs to still be able to trust certificates (provided there is a common CA in the chain, that is, a CA that is trusted by both parties).
The Certificate
In addition to your public key and the identity of the issuing CA, the issued certificate contains information about the purposes of your key and certificate. Furthermore, it includes the path to the CA's list of revoked certificates, and it specifies the certificate validity period (beginning and ending dates).
Assuming the certificate consumer trusts the issuing CA for your certificate, the certificate consumer must determine whether the certificate is still valid by comparing the certificate's beginning and ending dates with the current time and by checking that your certificate in not on the CA's list of revoked certificates.
The Certificate Revocation List
Assuming the certificate is being used in a valid time period and the certificate consumer trusts the issuing CA, there is one more item for the certificate consumer to check before using the certificate: the certificate revocation list (CRL). The certificate consumer checks the CA's CRL (the path to which is included as an extension in your certificate) to ensure your certificate is not on the list of certificates that have been revoked. CRLs exist because there are times when a certificate has not expired, but it can no longer be trusted. Periodically, the CA will publish an updated CRL. Certificate consumers are responsible for comparing certificates to the current CRL before considering the certificate trustworthy.
Your Public Key Used for Encryption
If a sender wants to encrypt a message before sending it to you, the sender first retrieves your certificate. After the sender determines that the CA is trusted and your certificate is valid and not revoked, the sender uses your public key (recall it is part of the certificate) with cryptographic algorithms to encrypt the plaintext message into ciphertext. When you receive the ciphertext, you use your private key to decrypt the ciphertext.
If a third party intercepts the ciphertext email message, the third party will not be able to decrypt it without access to your private key.
Note that the bulk of the activities listed here are handled by software, not directly by the user.
Your Public Key Used for Signature Verification
A digital signature is used as confirmation that a message has not been altered and as confirmation of the message sender's identity. This digital signature is dependent on your private key and the message contents. Using the message as input and your private key, cryptographic algorithms create the digital signature. The contents of the message are not changed by the signing process. A recipient can use your public key (after checking your certificate's validity, issuing CA, and revocation status) to determine whether the signature corresponds to the message contents and to determine whether the message was sent by you.
If a third party intercepts the intended message, alters it (even slightly), and forwards it and the original signature to the recipient, the recipient, upon examination of the message and signature, will be able to determine that the message is suspect. Similarly, if a third party creates a message and sends it with a bogus digital signature under the guise that it originated from you, the recipient will be able to use your public key to determine that the message and signature do not correspond to each other.
Nonrepudiation is also supported by digital signatures. If the sender of a signed message denies sending the message, the recipient can use the signature to refute that claim.
Note that the bulk of the activities listed here are also handled by software, not directly by the user.
Microsoft Certificate Services Role
Microsoft Certificate Services has the role of issuing certificates or denying requests for certificates, as directed by policy modules, which are responsible for ensuring the identity of the certificate requester. Certificate Services also provides the ability to revoke a certificate, as well as publish the CRL. Certificate Services can also centrally distribute (for example, to a directory service) issued certificates. The ability to issue, distribute, revoke, and manage certificates, along with the publication of CRLs, provides the necessary capabilities for public key infrastructure.
How to Export a Certificate and PrivateKey in PKCS #12 Format
C Generate Plain Key Exportable Certificate Template
You can create a file in PKCS #12 format to export private keysand their associated X.509 certificate to other systems. Access to the fileis protected by a password.
Find the certificate to export.
Export the keys and certificate.
Use the keystoreand label from the pktool list command. Provide a filename for the export file. When the name contains a space, surround the namewith double quotes.
Protect the export file with a password.
At the prompt,type the current password for the keystore. At this point, you create a passwordfor the export file. The receiver must provide this password when importingthe file.
Tip –Send the password separately from the export file. Best practicesuggests that you provide the password out of band, such as during a telephonecall.
Example 15–4 Exporting a Certificate and Private Key in PKCS #12 Format
Private Key Certificate Export
In thefollowing example, a user exports the private keys with their associated X.509certificate into a standard PKCS #12 file. This file can be importedinto other keystores. The PKCS #11 password protects the source keystore.The PKCS #12 password is used to protect private data in the PKCS #12file. This password is required to import the file.
C Generate Plain Key Exportable Certificate Online
C Generate Plain Key Exportable Certificate Format
C Generate Plain Key Exportable Certificate Free
The user then telephones the recipient and provides the PKCS #12 password.
Related Articles
- Steam Key Generator No Survey Media Lateral
- Windows Vista Premium Product Key Generator
- Generate Ssh Key For Filezilla Mac
- Generate Ssh Key Putty And Use In Centos
- Generate Rsa Crypto Key Cisco Command
- Generating Equivalent Numerical Expressions Module 10 Answer Key
- Generate Dkim Key G Suite
- Windows Xp 32 Bit Professional Product Key Generator
- Windows 8 Ultimate 64 Bit Product Key Generator