Generate Sas Key Service Bus
I am trying to generate Shared Access signature for the Azure service bus queue. The key should be the value. From code share above I can generate SAS token. The New-AzServiceBusAuthorizationRuleSASToken cmdlet generates a Shared Access Signature (SAS) token for an Azure Eventhub Namesapce or Azure Eventhub.
Syntax
Description
The New-AzServiceBusAuthorizationRuleSASToken cmdlet generates a Shared Access Signature (SAS) token for an Azure Eventhub Namesapce or Azure Eventhub
Examples
Example 1
Generate SAS token for the given authorixation rule for Namespace with start and expiry time.
Example 2
Our DKIM wizard generates the public / private 1024 bit key pair you need to setup DomainKeys/DKIM. This DKIM record generator also includes specific instructions on how to setup the Hurricane Server and your DNS server. How to Use this Domain Key Generator. To use the DKIM wizard, first specify a domain and a selector. The domain and the selector are not used in the generation of the public / private key pair. Generate a DKIM Core Key. Enter the domain you'd like to generate keys for, for example dkimcore.org and hit the button. This online wizard is fine for generating keys for testing and evaluation. If you decide to use DKIM Core in production, though, you might want to consider the security risks. Generate dkim key for domain. Yahoo originally created Domain Keys as an authentication and validation technique for email using a PGP-like protocol. The original specification has since been improved to DKIM (DomainKeys Identified Mail) by the community and a series of IETF standards resulted in RFC 6376. Nov 01, 2019 To create the DKIM signature, you will have to specify only two tags of all the above: an authorized domain (d=) and a selector (s=).
Generate SAS token for the given authorixation rule for Namespace with expiry time.
Parameters
ARM ResourceId of the Authoraization Rule
| Type: | String |
| Aliases: | ResourceId |
| Position: | 0 |
| Default value: | None |
| Accept pipeline input: | True (ByPropertyName) |
| Accept wildcard characters: | False |
Prompts you for confirmation before running the cmdlet.
| Type: | SwitchParameter |
| Aliases: | cf |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
The credentials, account, tenant, and subscription used for communication with Azure.
| Type: | Microsoft.Azure.Commands.Common.Authentication.Abstractions.Core.IAzureContextContainer |
| Aliases: | AzContext, AzureRmContext, AzureCredential |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Expiry Time
Crypto key generate rsa 2048. Navigate to Configuration Device Management Management Access ASDM/HTTPS/Telnet/SSH Add Select ASDM/HTTPS Supply the and subnet OK.
| Type: | System.Nullable`1[System.DateTime] |
| Position: | 2 |
| Default value: | None |
| Accept pipeline input: | True (ByPropertyName) |
| Accept wildcard characters: | False |
Key Type
| Type: | String |
| Position: | 1 |
| Default value: | None |
| Accept pipeline input: | True (ByPropertyName) |
| Accept wildcard characters: | False |
Start Time
| Type: | System.Nullable`1[System.DateTime] |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | True (ByPropertyName) |
| Accept wildcard characters: | False |
Shows what would happen if the cmdlet runs.The cmdlet is not run.
| Type: | SwitchParameter |
| Aliases: | wi |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Inputs
System.Nullable`1[[System.DateTime, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]]
Outputs
Microsoft.Azure.Commands.ServiceBus.Models.PSSharedAccessSignatureAttributes
Notes
RELATED LINKS
-->Applications gain access to Azure Service Bus resources using Shared Access Signature (SAS) token authentication. With SAS, applications present a token to Service Bus that has been signed with a symmetric key known both to the token issuer and Service Bus (hence 'shared') and that key is directly associated with a rule granting specific access rights, like the permission to receive/listen or send messages. SAS rules are either configured on the namespace, or directly on entities such as a queue or topic, allowing for fine grained access control.
SAS tokens can either be generated by a Service Bus client directly, or they can be generated by some intermediate token issuing endpoint with which the client interacts. For example, a system may require the client to call an Active Directory authorization protected web service endpoint to prove its identity and system access rights, and the web service then returns the appropriate Service Bus token. This SAS token can be easily generated using the Service Bus token provider included in the Azure SDK.
Important
Generate Sas Key Service Bus Line
If you are using Azure Active Directory Access Control (also known as Access Control Service or ACS) with Service Bus, note that the support for this method is now limited and you should migrate your application to use SAS. For more information, see this blog post and this article.
Azure Active Directory
Azure Active Directory (Azure AD) integration for Service Bus resources provides role-based access control (RBAC) for fine-grained control over a client’s access to resources. You can use role-based access control (RBAC) to grant permissions to security principal, which may be a user, a group, or an application service principal. The security principal is authenticated by Azure AD to return an OAuth 2.0 token. The token can be used to authorize a request to access an Service Bus resource (queue, topic, etc.).

For more information about authenticating with Azure AD, see the following articles:
Important
Authorizing users or applications using OAuth 2.0 token returned by Azure AD provides superior security and ease of use over shared access signatures (SAS). With Azure AD, there is no need to store the tokens in your code and risk potential security vulnerabilities. We recommend that you use using Azure AD with your Azure Service Bus applications when possible.
Shared access signature
SAS authentication enables you to grant a user access to Service Bus resources, with specific rights. SAS authentication in Service Bus involves the configuration of a cryptographic key with associated rights on a Service Bus resource. Clients can then gain access to that resource by presenting a SAS token, which consists of the resource URI being accessed and an expiry signed with the configured key.
You can configure keys for SAS on a Service Bus namespace. The key applies to all messaging entities within that namespace. You can also configure keys on Service Bus queues and topics. SAS is also supported on Azure Relay.
To use SAS, you can configure a SharedAccessAuthorizationRule object on a namespace, queue, or topic. This rule consists of the following elements:
- KeyName: identifies the rule.
- PrimaryKey: a cryptographic key used to sign/validate SAS tokens.
- SecondaryKey: a cryptographic key used to sign/validate SAS tokens.
- Rights: represents the collection of Listen, Send, or Manage rights granted.
Authorization rules configured at the namespace level can grant access to all entities in a namespace for clients with tokens signed using the corresponding key. You can configure up to 12 such authorization rules on a Service Bus namespace, queue, or topic. By default, a SharedAccessAuthorizationRule with all rights is configured for every namespace when it is first provisioned.
To access an entity, the client requires a SAS token generated using a specific SharedAccessAuthorizationRule. The SAS token is generated using the HMAC-SHA256 of a resource string that consists of the resource URI to which access is claimed, and an expiry with a cryptographic key associated with the authorization rule.
Generate Sas Key Service Bus Routes
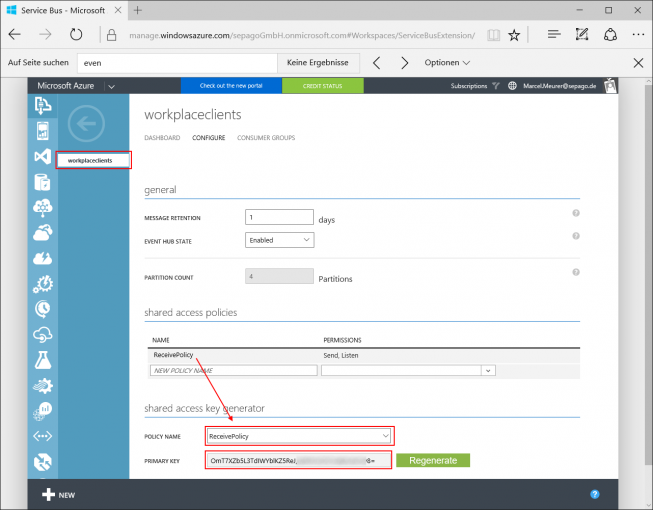
SAS authentication support for Service Bus is included in the Azure .NET SDK versions 2.0 and later. SAS includes support for a SharedAccessAuthorizationRule. All APIs that accept a connection string as a parameter include support for SAS connection strings.
Azure Storage Generate Sas
Next steps
- Continue reading Service Bus authentication with Shared Access Signatures for more details about SAS.
- How to migrate from Azure Active Directory Access Control (ACS) to Shared Access Signature authorization.
- Changes To ACS Enabled namespaces.
- For corresponding information about Azure Relay authentication and authorization, see Azure Relay authentication and authorization.